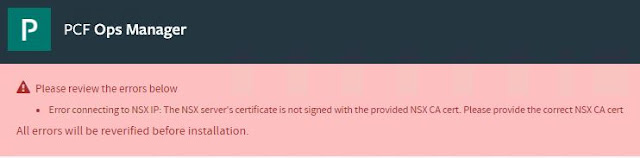
Issue / Problem Statement
If we
bosh scp directly to folders under /var/vcap/jobs/xxx/config, you will encounter Permission denied like:$ bosh -e lite -d concourse4 scp concourse.yml web:/var/vcap/jobs/uaa/config/ Using environment '192.168.50.6' as client 'admin' Using deployment 'concourse4' Task 3687. Done web/4de05ffc-ae08-4dfa-a52a-a751e62b624f: stderr | Unauthorized use is strictly prohibited. All access and activity web/4de05ffc-ae08-4dfa-a52a-a751e62b624f: stderr | is subject to logging and monitoring. web/4de05ffc-ae08-4dfa-a52a-a751e62b624f: stderr | scp: /var/vcap/jobs/uaa/config//concourse.yml: Permission denied
Interestingly, if we
bosh scp to some folders like `/tmp', it's fine:$ bosh -e lite -d concourse4 scp concourse.yml web:/tmp/ Using environment '192.168.50.6' as client 'admin' Using deployment 'concourse4' Task 3689. Done web/4de05ffc-ae08-4dfa-a52a-a751e62b624f: stderr | Unauthorized use is strictly prohibited. All access and activity web/4de05ffc-ae08-4dfa-a52a-a751e62b624f: stderr | is subject to logging and monitoring.
Let's verify it:
$ bosh -e lite -d concourse4 ssh web -c 'ls -la /tmp/' Using environment '192.168.50.6' as client 'admin' Using deployment 'concourse4' Task 3693. Done web/4de05ffc-ae08-4dfa-a52a-a751e62b624f: stderr | Unauthorized use is strictly prohibited. All access and activity web/4de05ffc-ae08-4dfa-a52a-a751e62b624f: stderr | is subject to logging and monitoring. web/4de05ffc-ae08-4dfa-a52a-a751e62b624f: stdout | total 2128 web/4de05ffc-ae08-4dfa-a52a-a751e62b624f: stdout | drwxrwx--T 4 root vcap 4096 Oct 27 13:27 . web/4de05ffc-ae08-4dfa-a52a-a751e62b624f: stdout | drwxr-xr-x 34 root root 4096 Oct 25 08:55 .. web/4de05ffc-ae08-4dfa-a52a-a751e62b624f: stdout | -rw-r--r-- 1 root root 233394 Oct 25 08:57 ca-certificates.crt web/4de05ffc-ae08-4dfa-a52a-a751e62b624f: stdout | -rw-r--r-- 1 bosh_99ef981c59fa482 bosh_99ef981c59fa482 2496 Oct 27 13:27 concourse.yml web/4de05ffc-ae08-4dfa-a52a-a751e62b624f: stdout | -rwxr-xr-x 1 root root 1923450 Aug 24 05:46 garden-init web/4de05ffc-ae08-4dfa-a52a-a751e62b624f: stdout | drwxr-xr-x 2 root root 4096 Oct 25 08:57 hsperfdata_root web/4de05ffc-ae08-4dfa-a52a-a751e62b624f: stdout | drwxr-x--- 2 vcap vcap 4096 Oct 25 08:57 hsperfdata_vcap web/4de05ffc-ae08-4dfa-a52a-a751e62b624f: stderr | Connection to 10.244.0.104 closed.
Yes, we can see that the file
concourse.yml has been successfully copied into our BOSH-managed VM node web.
Now if we really want to
scp file(s) to the right place under /var/vcap/jobs/xxx/config, how?Solution
As you have seen we can copy over to
/tmp, let's wrap it up with some more scripts.$ bosh -e lite -d concourse4 scp concourse.yml web:/tmp/ $ bosh -e lite -d concourse4 ssh web -c 'sudo cp /tmp/concourse.yml /var/vcap/jobs/uaa/config/'
Let's verify it again:
$ bosh -e lite -d concourse4 ssh web -c 'sudo ls -al /var/vcap/jobs/uaa/config/' Using environment '192.168.50.6' as client 'admin' Using deployment 'concourse4' Task 3699. Done web/4de05ffc-ae08-4dfa-a52a-a751e62b624f: stderr | Unauthorized use is strictly prohibited. All access and activity web/4de05ffc-ae08-4dfa-a52a-a751e62b624f: stderr | is subject to logging and monitoring. web/4de05ffc-ae08-4dfa-a52a-a751e62b624f: stdout | total 60 web/4de05ffc-ae08-4dfa-a52a-a751e62b624f: stdout | drwxr-x--- 3 root vcap 4096 Oct 27 13:34 . web/4de05ffc-ae08-4dfa-a52a-a751e62b624f: stdout | drwxr-x--- 5 root vcap 4096 Oct 25 08:56 .. web/4de05ffc-ae08-4dfa-a52a-a751e62b624f: stdout | -rw-r----- 1 root vcap 420 Oct 25 08:56 bpm.yml web/4de05ffc-ae08-4dfa-a52a-a751e62b624f: stdout | -rw-r--r-- 1 root root 2496 Oct 27 13:34 concourse.yml ... web/4de05ffc-ae08-4dfa-a52a-a751e62b624f: stderr | Connection to 10.244.0.104 closed.
Yes, we made it! The file has been copied to the desired folder, say
/var/vcap/jobs/uaa/config/.I also posted it in my gist, here.